
Jasper Sleet: The Remote Job Scam Tactics
Can you imagine that the “remote colleague” who joins your online meetings every day and works with you on projects is actually a spy sent by a hostile state? His mission is to earn income from your company, hand it over to his government, and when he leaves, casually steal some of your trade secrets.
This scenario is already playing out.
According to research by the think tank CSIS, this tactic—known as Jasper Sleet—generates at least $600 million annually for the North Korean government. North Korean IT workers steal American identities and use tools such as voice-altering technology to secure remote jobs at U.S. companies, funneling income directly into Pyongyang’s weapons of mass destruction programs.
In addition, these operatives often steal confidential information or transfer critical technology and assets back to their country. For example, one North Korean employee working at a blockchain company siphoned off cryptocurrency worth more than $900,000 at the time.
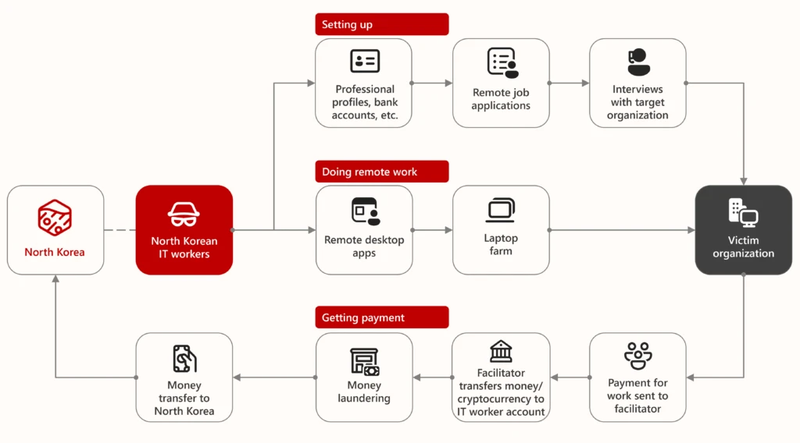
Of course, this operation could not be carried out by North Koreans alone—they require assistance from people on the ground. In late June, the Department of Justice issued a press release announcing that six Chinese nationals are suspected of helping IT workers tied to North Korea secure remote jobs.
These accomplices hiding inside the United States—the six indicted Chinese nationals and their associates—provided addresses, bank accounts, and fake U.S. identity documents. They also set up shell companies and fraudulent websites to promote the profiles of North Korean IT workers seeking remote jobs.
In October 2024, when law enforcement decided to move in, they simultaneously carried out searches at seven locations across California, New York, and New Jersey. Inside these registered offices, authorities discovered large numbers of laptops—so-called “laptop farms.” U.S.-based accomplices had provided the space to set up these farms, while North Korean workers remotely connected to the devices inside the United States to carry out their tasks and job responsibilities.

Media reports indicate that at least 300 U.S. companies were victimized, and even two U.S. government agencies were infiltrated. The severity of the situation forced authorities to launch a large-scale crackdown. The Department of Justice froze 29 financial accounts across 16 states, shut down 21 fraudulent websites, and seized 200 computers suspected of being involved in similar operations.
Not the First Case: China and North Korea’s Coordinated Cyber Assault
Chinese and North Korean hackers have long been accustomed to exploiting various loopholes in the United States to commit fraud and reap illicit profits. In addition to carrying out cyberattacks independently, they also share information and exchange resources with each other.
Chinese hackers have long been dedicated to attacking the United States, a fact well known to the public. One example is the frequent Volt Typhoon campaign, which targeted critical U.S. infrastructure such as water systems, power grids, ports, and airports, aiming to build the capability to cripple operations in a short time. Another notorious campaign, Salt Typhoon, attempted to infiltrate major U.S. telecom and internet providers to steal user data, intercept sensitive communications, and conduct surveillance. In fact, as recently as July this year, the Department of Homeland Security discovered that a state’s National Guard had been compromised by Salt Typhoon for nearly a year.
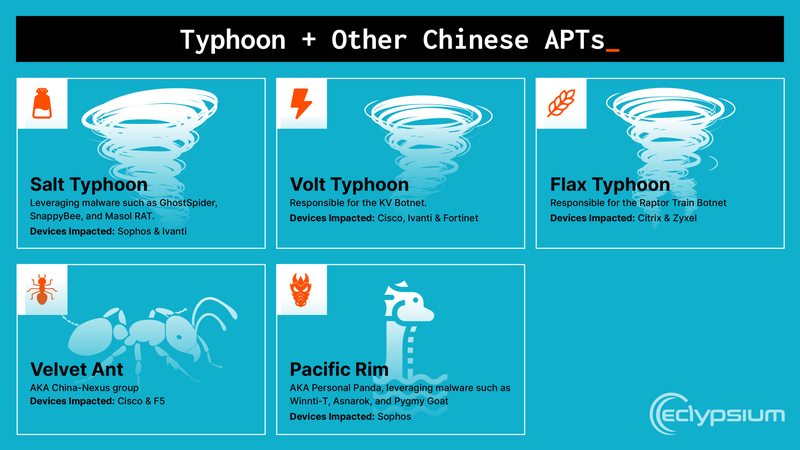
In July of this year, Microsoft reported that it had identified two Chinese state-backed hacking groups, “Linen Typhoon” and “Violet Typhoon,” exploiting security vulnerabilities in SharePoint, Microsoft’s collaboration and document management platform. The hackers allegedly used this flaw to attack several state government agencies, federal departments, as well as universities and energy companies.
In addition, the think tank CSIS released a report this July highlighting the close cooperation between China and North Korea in cyber operations. The report explained that because North Korea’s domestic internet infrastructure is relatively limited, it often carries out attacks through Chinese and Russian networks, masking the true origin of the operations and making accountability far more difficult to pursue.
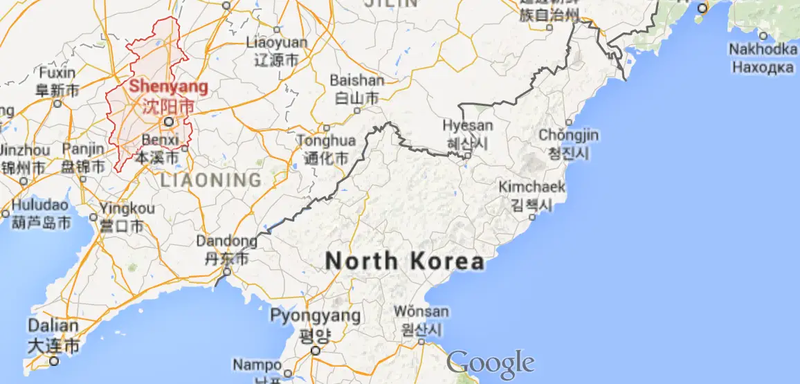
China has therefore provided North Korea with various infrastructure support. Several cities in northeastern China, including Shenyang, have been identified as key hubs for North Korean hackers conducting operations abroad. A decade ago, they even used IP addresses based in China to launch major cyberattacks against South Korea’s critical infrastructure, attempting to cripple water facilities and nuclear power plants.
Early last year, the Department of Justice officially announced charges against a North Korean national named Rim Jong Hyok. He was involved with a hacking group known as Andariel, which used ransomware to attack the U.S. healthcare system, attempting to hold hospitals and insurance providers hostage. The revenue generated from this series of cyberattacks was funneled back into North Korea’s defense and technological development programs, as well as to fund further hacking operations.
Prosecutors noted that these hacker groups, directed by the North Korean government, laundered their ransomware profits through intermediaries based in China. The illicit funds were then used to acquire new cyber equipment, enabling further intrusions to steal sensitive defense and technological intelligence. Subsequent victims of these attacks included two U.S. Air Force bases and the Office of Inspector General at NASA (NASA-OIG).
These organized, highly specialized, and technologically advanced cyberattacks demonstrate that they are being carried out with clear purpose and planning. The increasing frequency of such operations leaves little doubt about their objectives: to extract as much money, sensitive intelligence, and technology from the United States as possible—weakening America’s economic strength on one hand while narrowing the gap between the two sides on the other. The backing of state governments makes this all the more evident.

How to Protect Ourselves? Building Fraud Awareness and an International Cooperation Network
What we must clearly recognize is that China and North Korea’s hostility toward the United States is unfolding right before our eyes. No matter how courteous or polite Chinese leaders and officials may appear, or how much goodwill they claim to extend to America, they will never pass up an opportunity to undermine the United States in pursuit of China’s interests—as evidenced by their deployment of large numbers of spies and their tolerance of companies exporting fentanyl precursors to the U.S.
The CSIS report also makes it clear that the difficulty in combating transnational cybercrime lies in the lack of effective international cooperation. Even when the United States imposes direct or indirect sanctions on Chinese and Russian entities involved in North Korea’s cyber operations, the impact remains very limited—because they can always find new channels and new countries to bypass U.S. sanctions and restrictions. What we need is a multilateral cooperation framework to address accountability among third countries.
In 2024, the United Nations adopted the UN Convention on Countering Cybercrime with the aim of strengthening international cooperation and combating cybercrime. The convention defines various categories of cybercrime and imposes obligations on member states to collect and preserve electronic evidence. Parties are required to ensure that designated data within their jurisdiction is preserved and to allow lawful access by authorities under domestic law. Member states are also obligated to respond to requests from other countries regarding investigative cooperation, evidence preservation, and information sharing.

Even though Beijing has publicly expressed support, what we actually see is a lack of real effort to curb North Korea’s growing and increasingly brazen cybercrime activities. On the contrary, China has cooperated with North Korean hacker groups by providing infrastructure and money-laundering channels, enabling them to grow stronger. Worse still, Chinese state-backed hacking groups themselves continue to target U.S. companies and government agencies.
Therefore, we must implement the aforementioned regulatory mechanisms and strengthen international cooperation. More importantly, we need to expose China’s fingerprints in these cybercrimes, hold the Chinese government directly accountable, and tear off the false mask it hides behind.
China and North Korea have never abandoned their confrontation with the United States. They continue to siphon off America’s prosperity to enrich themselves and grow stronger. Only by fully recognizing their hostility can we rightfully strengthen countermeasures, expand frameworks for international cooperation, defend ourselves, and bring to justice those criminals hiding within our borders and sowing chaos in cyberspace.